Attacks on information system security (security attacks) often occur these days. Computer crime (cybercrime) in cyberspace is often carried out by a group of people who want to penetrate the security of a system. This activity aims to search for, obtain, change, and even delete information in the system if it is really needed. There are several possible types of attacks carried out by attackers, namely:
1. Interception, namely parties who do not have authority have succeeded in obtaining information access rights
2. Interruption, namely the attacker has been able to control the system, but not completely. The original admin can still log in.
3. Fabrication, namely the attacker has inserted a fake object into the target system
4. Modification, namely the attacker has damaged the system and has changed it as a whole
According to David Icove, judging from the security holes that exist in a system, security can be classified into four types:
1) Physical Security (Physical Security)
A security that covers the entire system along with the equipment, peripherals, and media used. Usually, an attacker will carry out wiretapping (the process of monitoring and tapping to obtain a password in order to have access rights). If it fails, then DOS (Denial Of Service) will be an option so that all services used by the computer cannot work. Meanwhile, the way DOS works usually turns off any service that is active or floods the network with a very large number of messages. In simple terms, DOS exploits a security hole in the TCP/IP protocol known as Syn Flood, namely that the target system will be flooded by a very large number of requests (flooding), so that access becomes very busy.
2) Data and Media Security
In this security, attackers will take advantage of weaknesses in the software used to process data. Usually, the attacker will insert a virus on the target computer via an attachment in an e-mail. Another way is to install a backdoor or Trojan horse on the target system. The goal is to obtain and collect information in the form of administrator passwords. This password will later be used to log in to the administrator account.
3) Security from outside parties
Taking advantage of the weakness or carelessness of influential people (having access rights) is one of the actions taken by a hacker or cracker to be able to enter the target system. This is usually called social engineering. Social engineering is the highest level in the world of hacking and cracking. Usually, people who carry out social engineering will disguise themselves as someone who uses the system and forgets the password, so they will ask the person who has access rights to the system to change or change the password that will be used to enter the system.
4) Security in Operations
It is a procedure for managing everything related to the security system after an attack. In this way, the system can run well or become normal again. Usually, attackers will delete all logs left on the target system (log cleaning) after carrying out an attack.
A firewall or firewall is a system or device that allows network traffic that is considered safe to pass through and prevents network traffic that is not safe. Generally, a firewall is implemented in a dedicated machine, which runs on the gateway between the local network and other networks. Firewalls are generally also used to control access to anyone who has access to a private network from outside parties or other data thieves. Besides that, a firewall is a method/system/mechanism that is applied either to hardware, software or the system itself with the aim of protecting, either by filtering, limiting, or even rejecting one or all relationships/activities of a segment on a private network with external networks that are not within its scope.
A firewall is a method or mechanism that is applied to hardware, software, or the system itself with the aim of protecting, either by filtering, limiting, or even denying one or all connections/activities of a segment on a private network with external networks that are not within its scope. The segment can be a workstation, server, router, or local area network (LAN). The use of firewalls is generally intended to serve:
1. Every individual's machine/computer is connected directly to an external network or the internet and wants everything on their computer to be protected.
2. A computer network consisting of more than one computer and various types of network topology used, whether owned by a company, organization, etc.
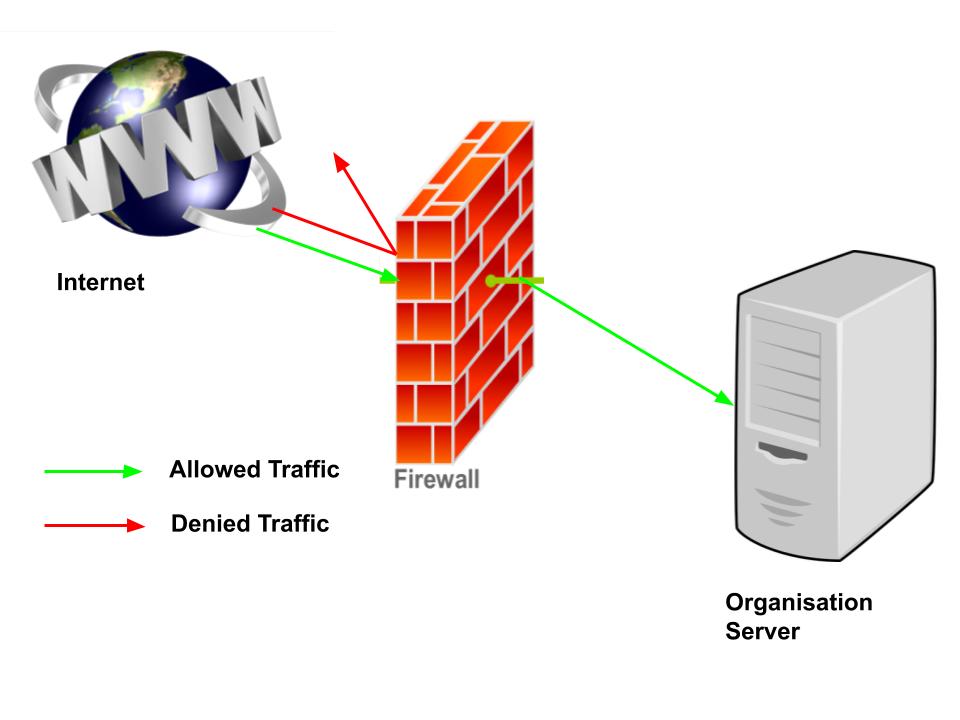
A firewall is a barrier between a local network and other public networks so that any incoming data can be identified for filtering so that data flow can be controlled to prevent danger/threats coming from the public network as in the following illustration.
A firewall can also monitor connection state information to determine whether it will allow network traffic. Generally, this is done by maintaining a connection state table (in firewall terms: state table) that monitors the state of all communications passing through the firewall. In general, the Firewall function is to:
1. Organize and control traffic.
2. Authenticate access.
3. Protect resources in a private network.
4. Record all incidents, and report them to the administrator
Firewall types can be grouped into four, namely:
1. A Personal Firewall is designed to protect a computer connected to a network from unwanted access. This type of firewall has recently evolved into a collection of programs that aim to completely secure the computer, for example, Microsoft Windows Firewall
2. Network Firewall is designed to protect the network as a whole from various attacks. Generally found in two forms, namely a dedicated device or as software installed on a server. For example: Internet Security and Acceleration Server (ISA Server), Cisco PIX
3. IP Filtering Firewall: An IP Filtering firewall works at the packet level
4. Proxy Server: How a proxy server works, it can be seen that when a user connects to a proxy server with client software, the proxy server will duplicate the communication.
إرسال تعليق